Current deception system objectives are contingent upon adversaries engaging with typically passive, unused deceptive elements, where skilled attackers can often detect and bypass such traps. Frenetik deceives adversaries by actively modifying and rotating real in-use user identifiers and assets, ensuring your deception plans are unavoidable.
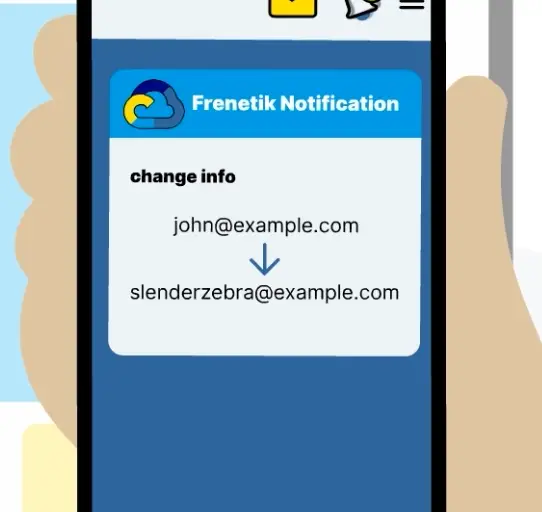
Keep adversaries guessing, stuck in a targeting loop of always-moving real login usernames and fully qualified domain names.
Leverage counter-reconnaissance by invalidating expired sessions and tokens whenever usernames or assets are updated/modified/moved, neutralizing the risk of ill-gotten credential and asset information. Any attempts to utilize outdated usernames or assets fail, and are actively tracked, flagged, and analyzed as potential reconnaissance or compromise attempts.

Have questions or need help? Reach out to learn how Frenetik can enhance your security.